Software-as-a-service (SaaS) has emerged as a pan-industry force by just about every estimation. SaaS has been bucking many of the venture slowdown trends, while data from Gartner indicates that SaaS constituted the lion’s share ($123 billion) of cloud end-user spending ($332 billion) last year.
But the pervasiveness of SaaS, and ease-of-access ushered in by the broader cloud movement, has created a beast that has come to be known as SaaS sprawl, with some companies accessing as many as 200 applications via the browser. Such stats bode well for any up-and-coming SaaS startup, but for companies that use the software, it raises a number of important security questions — how do they keep on top of things, and ensure that their employees are adopting strong security hygiene?
This is something that London-based Push Security is setting out to solve, with a platform that enables employees to use whatever SaaS apps they need for their jobs, without compromising basic security principles.
“Like it or not, SaaS apps now form part of a company’s infrastructure, but many don’t even know what does and doesn’t exist, and it’s growing continuously,” Push Security co-founder and CEO Adam Bateman told TC.
The company officially launches out of stealth today with $4 million in seed funding led by Decibel, with participation from notable angels including Duo Security co-founder Jon Oberheide.
How it works
The initial setup involves connecting Push Security to Office 365 or Google Workspace, which imports the company’s employee profiles and reviews their security status.
“This is our starting point because then the platform knows who it needs to initiate conversations with,” Bateman said.
Push then prompts employees to install a browser extension, which serves to identify the extent of a company’s SaaS sprawl — and any security issues therein.
Managers or IT personnel can see all SaaS across the company in a dashboard, along with the number of users. This data is also presented in individual employee dashboards, showing exactly who is using what SaaS and the browsers they are using to access it, while highlighting instances where they are using the same password across multiple services.
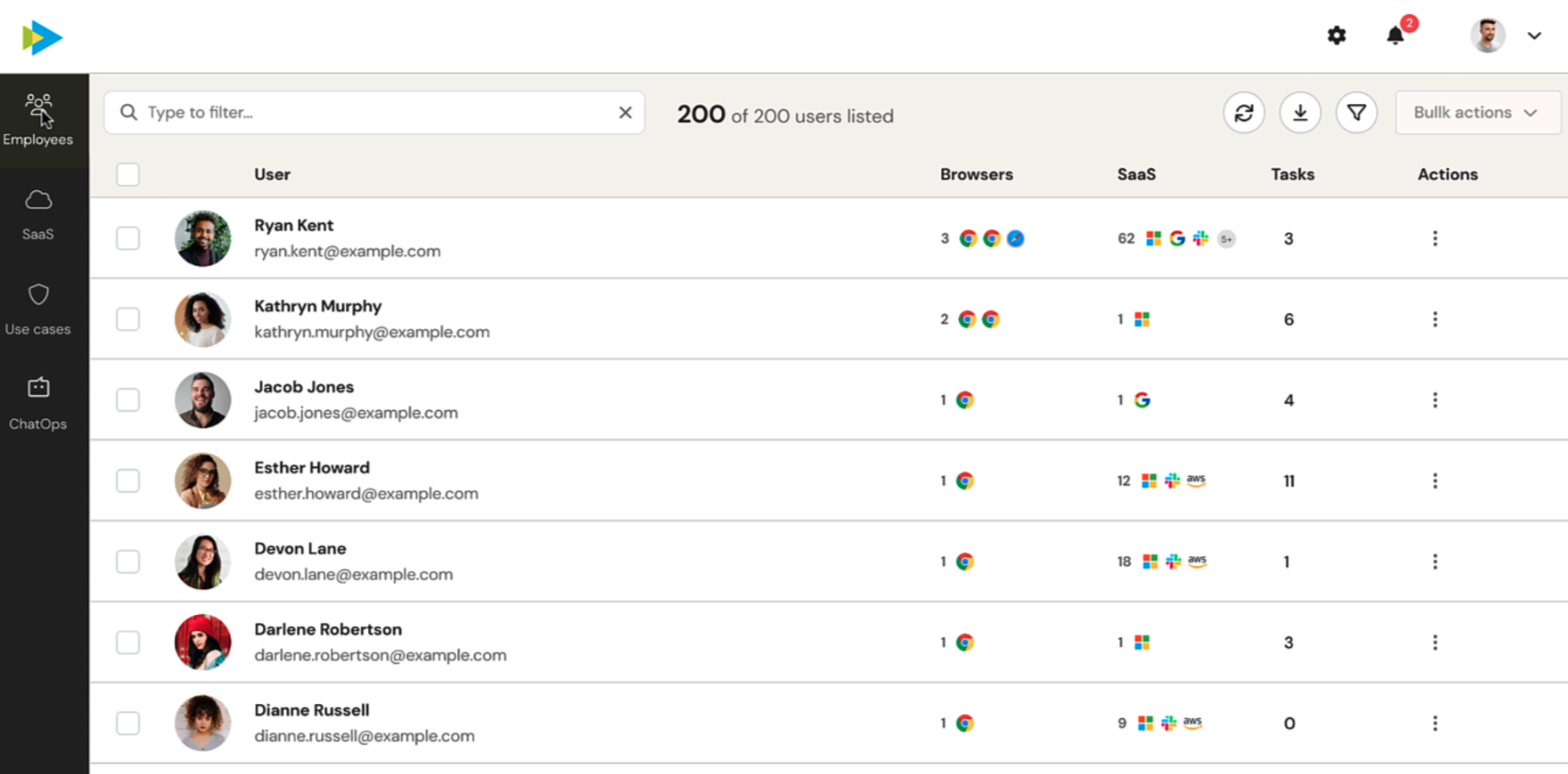
Employee SaaS dashboard. Image Credits: Push Security
Push can identify all the SaaS apps and associated security issues, such as weak or repeated username and password logins, as well as any third-party integrations, extensions and bots that workers have enabled in those applications.
Using chatbot-style prompts that can be integrated into communication tools such as Slack, Push can guide users through important security procedures such as setting up two-factor authentication (2FA), or prompting them to improve their passwords or activate specific security settings within an app.
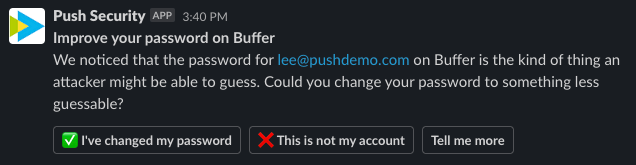
Push Security prompt. Image Credits: Push Security
Shadow IT
The core underlying problem that Push is looking to fix is what is known as “shadow IT,” which is when employees use software and systems without explicit approval from IT — it’s a practice that has become much easier in the world of SaaS.
Indeed, it has become much harder for IT and security teams to vet and scrutinize every application an employee wants to use to get their job done, given that they can sign up for just about any piece of software. And usually it’s well-intentioned, for example a worker might just want to trial a SaaS application as a precursor to convincing the powers-that-be that it’s worth investing in. But when they do that of their own volition, it often means weak passwords and a failure to activate any form of security controls such as 2FA.
In practice, this could mean that marketing teams test-driving third-party social media management tools could inadvertently jeopardise the company’s Twitter and Facebook accounts, or admins could dabble with mobile device management (MDM) software and create an easy inroad for hackers to deploy malware to mobile devices across the workforce.
While it’s true that companies can go some way toward preventing this by enforcing strict IT policies and oversight, it’s never completely fool-proof — and it’s not always entirely productive, either.
“It frustrates your employees who want to use their preferred tools and features,” Bateman said. “And moreover, if your competitors are allowing more SaaS in their companies, their employees are able to work faster and get products and features out the door quicker than yours can. You’re essentially hamstringing your employees from being as productive as they could be.”
While there are other shadow IT discovery tools on the market, they are generally all about giving IT and security teams the data to restrict SaaS usage. Push is designed to support SaaS usage, and make it more secure.
“To us, the key thing is that by working directly with the employees, we can build mutual trust over time and let them continue to freely adopt the tools they want without raising alarm bells from their security team,” Bateman said. “The security team will know employees are logging in securely and being responsible with their SaaS use, and they won’t have to be a blocker or an enforcer anymore. Win-win.”
The story so far
All three co-founders hail from another security company called MWR Infosecurity, which F-Secure acquired in a $106 million deal four years ago. Some 18 months later, the trio departed to launch Push Security without a specific idea in mind — the plan was simply to figure out what problem they were going to tackle after conducting some market research. And in March last year, they soft-launched an MVP and invited people into an early access preview.
“This was simply to allow us to have more meaningful conversations, hone in on the exact problem we were going to solve, and test our market messaging to understand what would resonate and bring people into the app,” Bateman said.
Last August, they set about trying to raise capital, and closed a $4 million seed round of funding, though they elected to only announce that today, alongside the platform’s full launch.
The underlying ethos — enlisting the help of employees in securing a company’s infrastructure — is shared by other companies. Kolide, for example, recently raised $17 million to bring a more user-focused approach to device security, such as prompting users if their laptop is running out of disk space, or customer data export files are sitting untouched in the downloads folder. And the general idea with Push is the same — security by cooperation, rather than diktat.
“We are strong advocates that security teams ‘enforcing and blocking’ employees is a thing of the past,” Bateman said. “Today, security is about enabling the business and its employees to move fast, safely and securely.”
The founders are well-accustomed to providing security support and services to some of the world’s biggest companies in their previous roles, but with Push it’s all about bringing the type of user-centric security that larger enterprises are already deploying internally to smaller businesses. While it wasn’t at liberty to divulge any early customer names, it did say that it was working with businesses across fintech, security, insurance, pharmaceutical and retail, among others.
“We spent our lives securing large enterprises so wanted to focus on taking security to the [other] 99%,” Bateman said. “We built this so that it’s accessible to SMEs and companies with fewer than 2,000 employees. But we are getting interest from larger companies as well. The cool thing to us is that we’ve got companies with 16,000 employees down to those with just 10-12 employees, which means we’re accessible to everyone trying to solve these problems.”






![Read more about the article [Funding Alert] Edtech startup Quizizz raises $12.5M in Series-A round led by Eight Roads Ventures](https://blog.digitalsevaa.com/wp-content/uploads/2021/03/Imageog0c-1615276233825-300x150.jpg)