Current estimates say that 70 – 90% of software uses open source. But how secure is open source? Open source packages are shared by developers globally, so using open source in your own applications means introducing third-party code into your projects. This can introduce security risks, and the more widely used any open source package is, the bigger the impact a security vulnerability inside it can have.
A new research project by Snyk and the Linux foundation focused on how organisations are securing their open source packages. The project looked at how developers detect and address risk. A thorough analysis of the data collected revealed some major missteps that organisations are taking when it comes to open source security. Here are three steps that organisations can take to fix those missteps and get on the path to stronger security practices around open source.
1. Understand that dependencies bring complexity
The average project has 49 vulnerabilities spanning 79 direct dependencies.
Open source security becomes a bigger challenge as the software supply chain becomes more complex. Nearly all modern applications are built with components that depend on other components, creating a supply chain that involves hundreds of components and multi-tiered dependencies.
The software supply chain is an attractive entry point for malicious actors because they can take advantage of vulnerabilities in small libraries that are widely used. Remember Log4Shell? It made any incoming data that gets logged vulnerable to RCE (remote code execution) attacks. It was a critical weakness inside of a popular open source logging framework — a vulnerability inside of a dependency.
Only 24% of organisations are confident in the security of their direct dependencies. And while 37% of organisations report that dependencies are easy to track, these dependencies are not necessarily in a secure state.
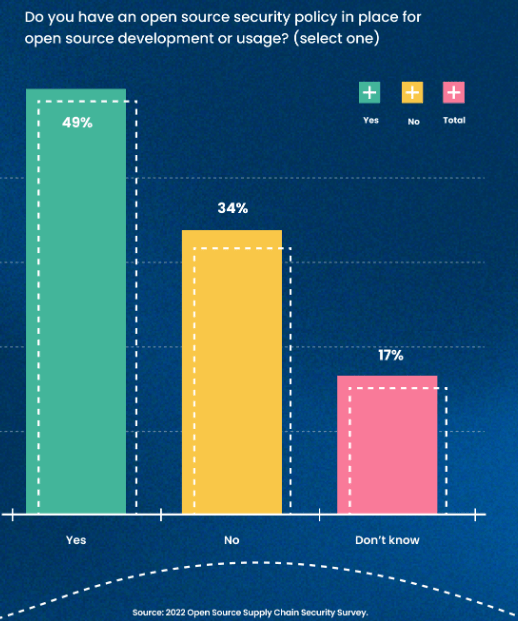
2. Lay the groundwork with security policies
Only 49% of organisations have a security policy that explicitly addresses the development and use of open source packages.
This is understandable in smaller organisations, where resources are limited. Research also showed that 27% of medium-to-large companies don’t have an established security policy in place. When you consider how much data each of these companies might be processing, 27% is an alarming statistic.
Every organisation needs a CISO (chief information security officer) or a person or team tasked with key security responsibilities. When key CISO capabilities are present and available, an open source security policy will follow. Actionable policies must be put in place and socialised across teams — starting with CISOs and developers, and moving throughout the organisation.
3. Use the right tools
73% of organisations are searching for best practices to improve their software security.
Organisations need to invest in a diverse set of tools to help them build more secure applications. In many cases, SCA (software composition analysis) tools can provide a strong advantage by enabling teams to find vulnerabilities in open source packages and learn how to fix them. Some organisations use other tools depending on their preferences regarding security testing.
SAST (static application security testing) tools, in use at 35% of organisations, scan source code, bytecode, and binary code in order to identify problematic coding patterns. Some organisations use an IaC (infrastructure as code) model to help developers write secure HashiCorp Terraform, AWS CloudFormation, Kubernetes, and Azure Resource Manager (ARM) configurations before touching production. IaC configurations fit security best practices directly into development workflows.
Each of these tooling options can help organisations take a big step toward prioritising open source security.
The combined power of education, policy, and tools
Using open source packages safely requires a new way of thinking about developer security that many organisations have not yet adopted. Knowing what risks exist in open source packages, and understanding how to build protection against those risks, can empower your organisation to use open source technology efficiently and safely. Finding the most effective tools and policies for open source security is a great place to start.
Catch our interview with Paul Down, Head of Sales at Intigriti.