As our lives get more and more digitally connected, every action is monitored and collected by multiple entities, used to train multiple AI models, stored across borders, sold to whoever is willing to pay for our data, and finally used to predict and manipulate our own thoughts and decision making.
Privacy regulations are being put in place across the globe to address this very problem. Privacy has been recognised as a fundamental human right and its abuse is a critical problem for digital societies.
The era of privacy regulations
The General Data Protection Regulation (GDPR) was an important milestone in recognising that privacy is a fundamental problem globally. It set the stage for privacy norms across the world by making penalties as high as 4% of global revenue of organisations violating user privacy in the region.
Following the EU’s GDPR, more than 120 countries around the world have either passed a new privacy regulation or are in the process of drafting and passing a new law protecting their citizens’ privacy.
Given that privacy is a new responsibility, most new-generation privacy regulations mandate large businesses to appoint a Data Protection Officer (DPO) to take care of an organisation’s privacy compliance requirements.
The challenges of being a DPO
Bringing behavioural change is always difficult, that too in an organisation whose business model and practices have been using personal data. DPOs have an unenviable job with mounting regulatory pressure and opaque business data usage models. Here are the are five key challenges they face in today’s ecosystem:
1. Awareness – Not many stakeholders understand privacy
2. Products – Non-availability of necessary technologies, products, and solutions for meeting privacy compliance requirements and ever-increasing data storing, sharing, or processing requests
3. Hidden flow – Personal data is handled and shared by many across the hybrid multicloud infrastructure of an organisation, which is opaque to the system
4. Culture – Privacy is a culture, which is non-existent today in many organisations and the DPO has to create it.
5. Business model – In some really challenging situations, for the existing business model to work, some privacy compromises are necessary or there is a need to create a new privacy-compliant business model, which may not be in the DPO’s control.
How does PrivaSapien help?
Using pioneering privacy enhancing technologies, PrivaSapien enables DPOs/ CISOs/ Data Analytics teams to visualise and mitigate privacy risk in data pipelines and data lakes so that data can be unlocked for business value creation through analytics and strategic business decision making.
PrivaSapien’s Privacy X-Ray and Event Horizon help businesses to address privacy challenges in an auditable, repeatable, and quantifiable way, accelerating privacy decision making.
The award-winning process of privacy risk visualisation and mitigation, using Privacy X-Ray and Event Horizon, can significantly accelerate the privacy journey of organisations with 4,000x faster privacy risk assessment, while enhancing utility of data by 90% compared to other contemporary methods. It enables addressing five business problems faced by DPOs in the following ways.
1. Awareness – Privacy X-Ray is the first-of-its-kind privacy risk visualisation product globally, which does privacy attack simulation based on global regulatory requirements and provides a unified privacy risk score along with risk mitigatory recommendation.
2. Products – Based on the visualised privacy risk, context based anonymisation of sensitive data can be designed and automated with Event Horizon. With this, entire data flows can be made private by design, which is measurable and auditable.
3. Privacy aware flow – Privacy X-Ray can help businesses visualise privacy risk in data flow and Event Horizon can enable privacy preservation of data based on context of downstream flow of data. Thus data pipelines and data lakes can be made privacy compliant.
4. Culture – To set a privacy-friendly culture in an organisation, a DPO needs to gain support of key stakeholders, make everyone aware of privacy risks and programme benefits, prove that privacy can be of strategic advantage, and establish that privacy can be a profit centre rather than just a compliance checkmark. With these products, businesses can implement privacy by design, which can accelerate customer’s digital trust and the need for a privacy-first culture.
5. Business model – New data-centric business models can be created by visualising privacy risk using Privacy X-Ray and context-based anonymisation using Event Horizon. Thus, rivacy engineering can create new streams of revenue for organisations rather than being a cost centre.
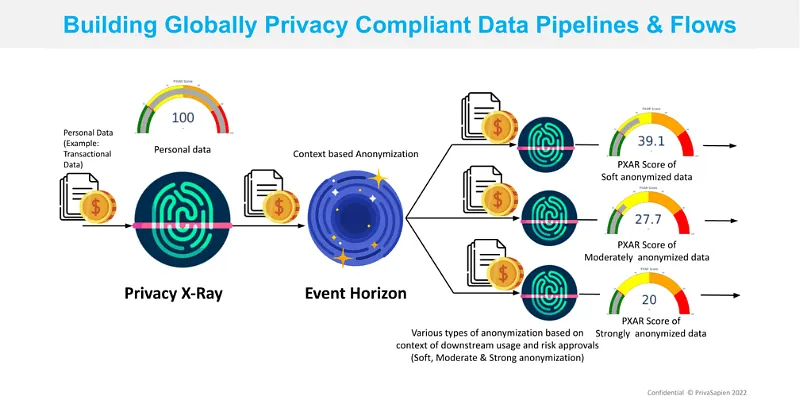
[ Example Scenario: A financial transaction dataset needs to be shared with multiple downstream parties – say an insurance, marketing, and loan processing team. With “DPIA”, “privacy by design” and “data minimisation” requirements, Privacy X-Ray can be used to visualise privacy risk. Event Horizon does context-based anonymisation to reduce the privacy risk based on various downstream contexts, following which Privacy X-Ray ensures mitigation of privacy risk before sharing data.]
Cohort 11 of NetApp Excellerator
PrivaSapien is a part of cohort 11 of the NetApp ExcellerateHER Program. A deeptech company with a woman co-founder, the team is looking forward to being mentored by global tech leaders as part of NetApp ExcellerateHER program.
With privacy regulations emerging globally, businesses are finding it difficult to design their privacy journey, meeting complex privacy requirements in their data lakes and data pipelines. Integrating NetApp’s deep expertise in data management and hybrid cloud data services with PrivaSapien’s pioneering privacy engineering solutions can empower customers to create privacy-complaint data ecosystems, which can be a strategic differentiator in gaining the end user’s trust.